- Published on
The 10 Biggest Crypto Hacks of 2024
- Authors

- Name
- Administrator
- @airdropdecks
Although 2024 will see a huge development in security technology, hackers are also constantly upgrading their attack techniques, turning every smallest vulnerability into an opportunity to steal billions of dollars.
2024 is a challenging year for the crypto industry as hacks and security exploits continue to increase with total losses reaching nearly $2,200 billion, up more than 22% from 2023's $1,800 billion.
The attacks focused on vulnerabilities in centralized exchanges such as Bitcoin DMM, WazirX, BingX, and DeFi protocol design flaws. In addition to financial targets, some of the attacks have a political element, and North Korea's Lazarus Group is suspected of being behind many of the major incidents.
Bitcoin DMM: $300 million
In May 2024, DMM Bitcoin, the Japanese crypto exchange, lost more than 4,500 BTC (worth more than $300 million).
The reason is believed to be related to the theft of private keys or “address poisoning”. This is the 8th largest hack in crypto history and the largest since the FTX incident in 2022.

WazirX: $230 million
On July 18, 2024, WazirX was hacked with a loss of $230 million. Hackers exploit weaknesses in multi-signature wallets by manipulating the interface of the Liminal platform, causing malicious transactions to be approved. Lazarus Group is suspected of being the team behind the hack.

Although WarziXX has tried to compensate users of the platform with a variety of bonus programs and promises to return the money, the project's WRX token still suffers. Binance de-listing. This makes WarZirX increasingly illiquid due to the large amount of assets in the fund coming from WRX tokens.
The Munchables: $62 million
In March 2024, the play-to-earn game Munchables on the Blast Layer 2 blockchain was exploited due to a vulnerability in the smart contract. Hackers taking advantage of proxy contracts can upgrade, insert malicious code and take in more than $62 million. After that, the property was recovered when the hacker returned the private key.

Dai whale exploit: $55 million
In August 2024, a crypto whale lost 55 million Dai stablecoins due to a phishing attack. Hackers take control of Decentralized Service Proxy (DSProxy) and use it to exploit the victim's Maker Vault.

Radiant Capital: $51 million
In October 2024, Radiant Capital was hacked for the second time with $51 million in losses. Hackers take advantage of a flaw in the 3-of-11 multi-signature mechanism, tricking signers into signing malicious transactions. Lazarus Group continues to be suspected of involvement.

The hacker has combined many skills including writing smart contract codes, using Trojan software to interfere with hard wallets, understanding the process of signing transactions, and planning to launder money to get out of the system.
BingX: $43 million
On September 20, 2024, Bing X was hacked to lose $43 million. Hackers target hot wallets and use multiple addresses to transfer stolen assets to Ethereum.
The stolen funds were transferred through numerous small transactions, suggesting that this was a well-planned and highly coordinated attack. BingX then took measures to fix the problem, which includes increased security and attempts to trace the stolen funds.
Penpie: $27 million
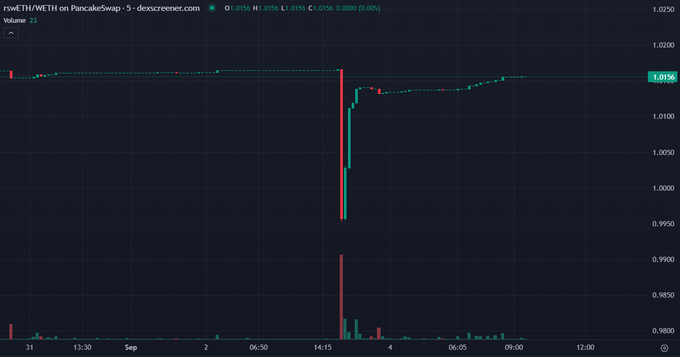
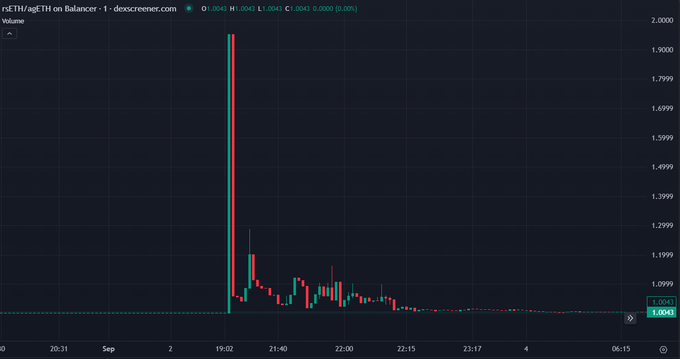
In September 2024, Penpie was exploited with a reentrancy attack, tricking the system into accepting fake tokens and withdrawing more than 27 million USDs in the form of rSWEth, wstETH, agETH and susDE. Hackers laundered money through Tornado Cash.
In terms of market impact, the sale of stolen assets has caused some minor changes in exchange rates. Specifically, wstETH and susDE were virtually unaffected when trading on Uniswap V3 and Curve. However, RSWETH suffered a slight devaluation on PancakeSwap, and AgeTH was significantly depeg on Balancer.
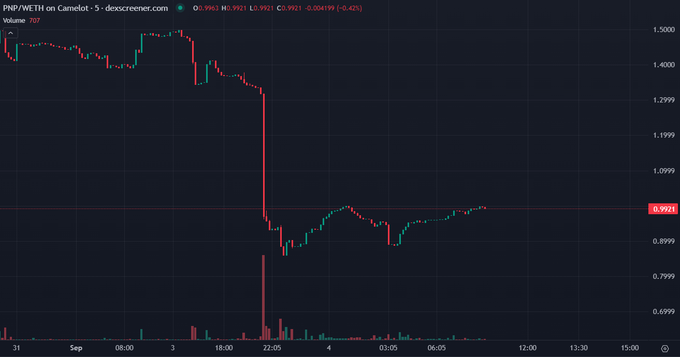
Meanwhile, Penpie's PNP token plummeted by as much as 40 percent, reflecting a drop in investor confidence in the project. In contrast, Pendle's PENDLE token was not affected in value compared to ETH, affirming that the Pendle protocol bears no direct impact or liability in this incident.
UWu Lend: $20 million
In June 2024, UwU Lend, a decentralized lending platform, became the target of an attack that exploited a vulnerability in the oracle pricing mechanism, causing about $20 million in damage.
This attack relies on how UwU Lend uses price data from liquidity pools on Curve Finance, especially for stablecoin SusDe. Hackers have cleverly manipulated the price of SusDe, disrupting the system and seizing assets.

Hackers start by making a flash loan, which allows them to borrow large amounts of assets in a short time without collateral. They then use this loan to execute a series of transactions in Curve's liquidity pool, reducing the value of SusDe.
When the price of SuSDE plummeted, hackers borrowed large amounts of SuSDE from UwU Lend, using other assets as collateral at a higher value than their real value at the time.
Sonne Finance: $20 million
In May 2024, Sonne Finance, a decentralized lending platform on Optimism layer 2, was seriously hacked, resulting in approximately $20 million in losses. This attack exploits a flaw in Sonne's design, which is a fork of Compound v2, highlighting the common risks of fork protocols that are not thoroughly secured.

In this attack, hackers sent a small amount of assets into an empty market on Sonne Finance, causing a large change in the exchange rate between the underlying asset and the token. They then exploit rounding errors in smart contract calculations to draw more assets than the number they originally deposited.
By repeating this process, hackers have hijacked about $20 million from the protocol.
M2 Exchange: $14 million
In October 2024, M2 Exchange in the UAE was hacked and lost nearly $14 million. The hackers attacked the hot wallets, causing the exchange to use its own assets to reimburse customers.

Hackers exploited a security vulnerability in M2 Exchange's system, infiltrating and taking control of hot wallets. They withdrew assets from wallets and transferred money through various wallet addresses to hide traces.